Hello, 1337 h44xors. Today, I'm going to talk about HTTPS. We can summarize HTTPS in one sentence: "HTTPS is just HTTP + a layer of encryption." In fact, this is true, but to understand the World Wide Web, we need to understand what that "layer of encryption" is.
HTTPS Overview
The HTTPS protocol was created to address one of the major issues with the HTTP protocol: the absence of encryption. The lack of encryption in HTTP communications creates an opportunity for a malicious actor to perform a Man-in-The-Middle attack. If you don't remember the purpose of this attack, here's a little reminder:
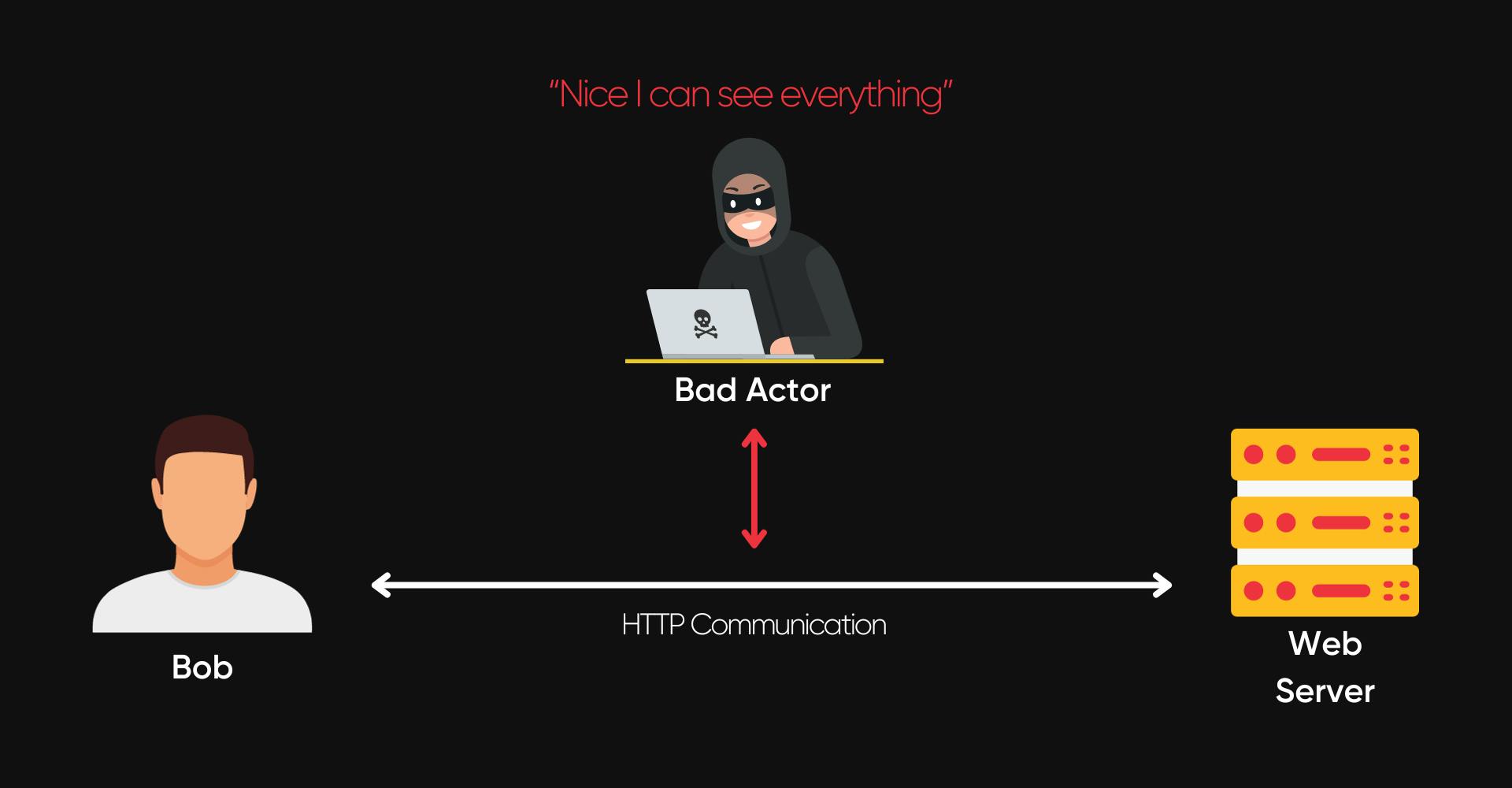
If we examine an HTTP request with a packet sniffer like Wireshark, we can observe what's happening live. In other words, a packet sniffer allows us to see the communications as they are sent to the server and vice versa. How cool is that ? 🔥
HTTP Packets vs HTTPS Packets
Here is an HTTP request captured with Wireshark :
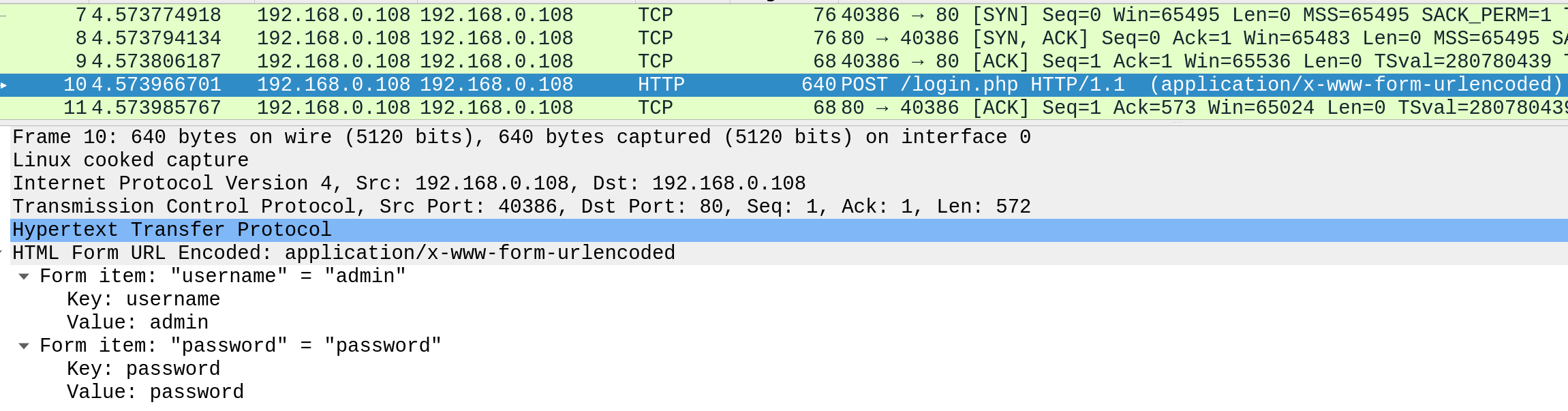
Can you understand it ? In the HTTP screenshot, you can see the login and password that Bob typed in the login form in clear text because of the lack of encryption.
Here is an HTTPS request captured with Wireshark :
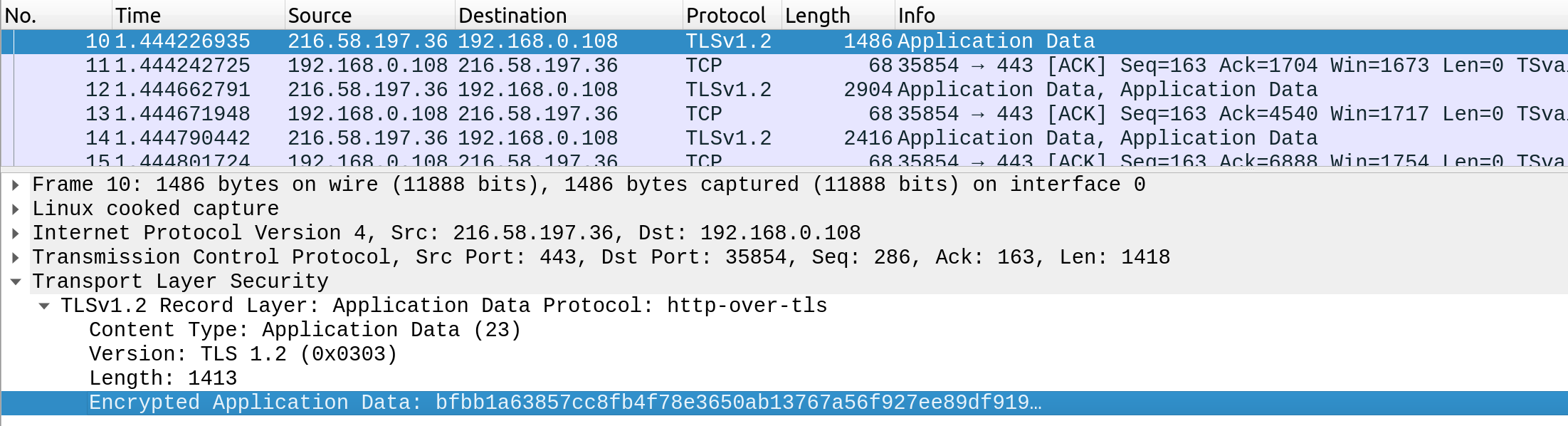
Now look at closely the last line. Can you understand something ? No ? This is because of encryption. This is what a bad actor will see if he try to sniff the communications between Bob and the web server.
The Transfert Layer Security Protocol
Look at this line. This is important to understand the HTTPS protocol.
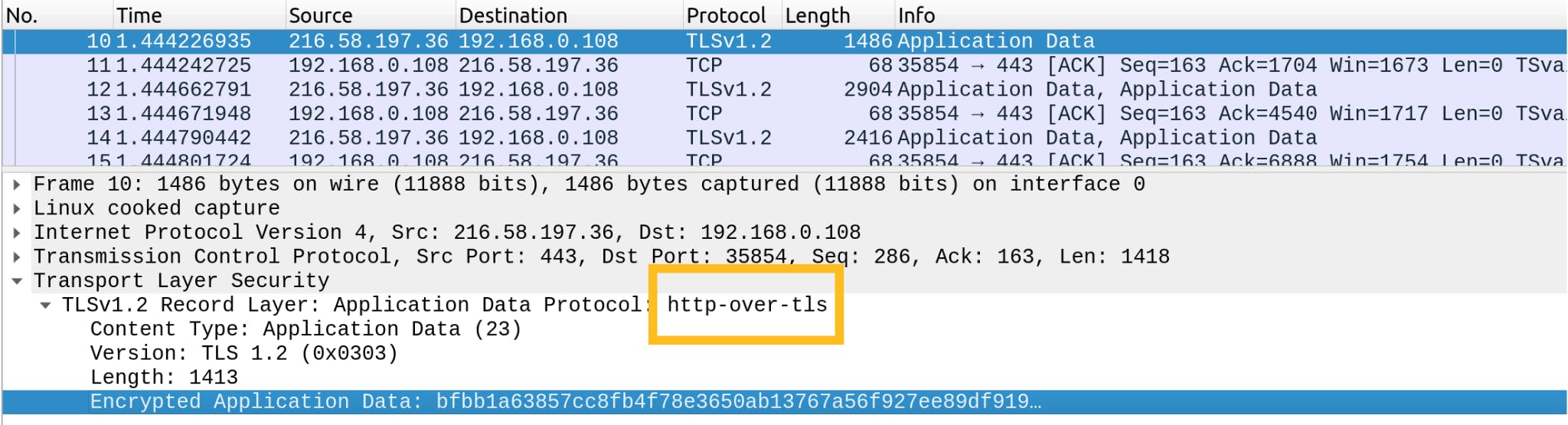
"http-over-tls" what is this line, what does it mean ? Basically "http-over-tls" means "http + a layer of encryption". TLS (Transfert Layer Security) is the protocol used today to ensure the encryption of data which is based on its predecessor, the SSL protocol.
Note : Since 2014, Google has taken into account whether a website uses HTTPS or not, for SEO purposes.
Websites that enforce the use of HTTPS can be identified by the use of https:// (e.g. https://beesploit.hashnode.dev at the beginning of the URL and the closed padlock icon in the search bar to the left of the URL).

Data sent between a client and a web server is encrypted with HTTPS, but it is possible to find out which URL has been visited if you use an unencrypted DNS. There are a few encrypted DNS services available, and here is a list:
Google DNS (8.8.8.8 and 8.8.4.4)
Cloudflare DNS (1.1.1.1 and 1.0.0.1)
OpenDNS (208.67.222.222 and 208.67.220.220)
Quad9 DNS (9.9.9.9)
Using encrypted DNS can help protect your privacy (trust the Google's one at your own risk) by preventing eavesdropping on your DNS queries, which can reveal the websites you visit.
Certificate and Certificate Authority
A Certificate Authority (CA) is a trusted entity that plays a major role in securing data, particularly in the context of the HTTPS protocol. The purpose of a CA is to issue a certificate that can prove the identity of an entity, in other terms the certificate says "This entity (server) is one you are trying to reach, this is not a fake and this certificate, issued by a known Certificate Authority is here to prove it".
There are plenty of Certificate Authorities :
Digicert
Let's Encrypt
IdenTrust
...
It is possible to create a self-signed certificate, however, you need to understand that only Certificate Authorities because of the trust they have earned, are legion on the Internet.
CAUTION: A website with "https://" is not enough to be considered as "secure". An attacker can create a website with a front end similar to a legit website, set a domain name like "faceboook.com" instead of "facebook.com", create a certificate for "faceboook.com" and the URL will be "faceboook.com" with 3 "o". An unaware person may think that this is the real website.
HTTPS Flow
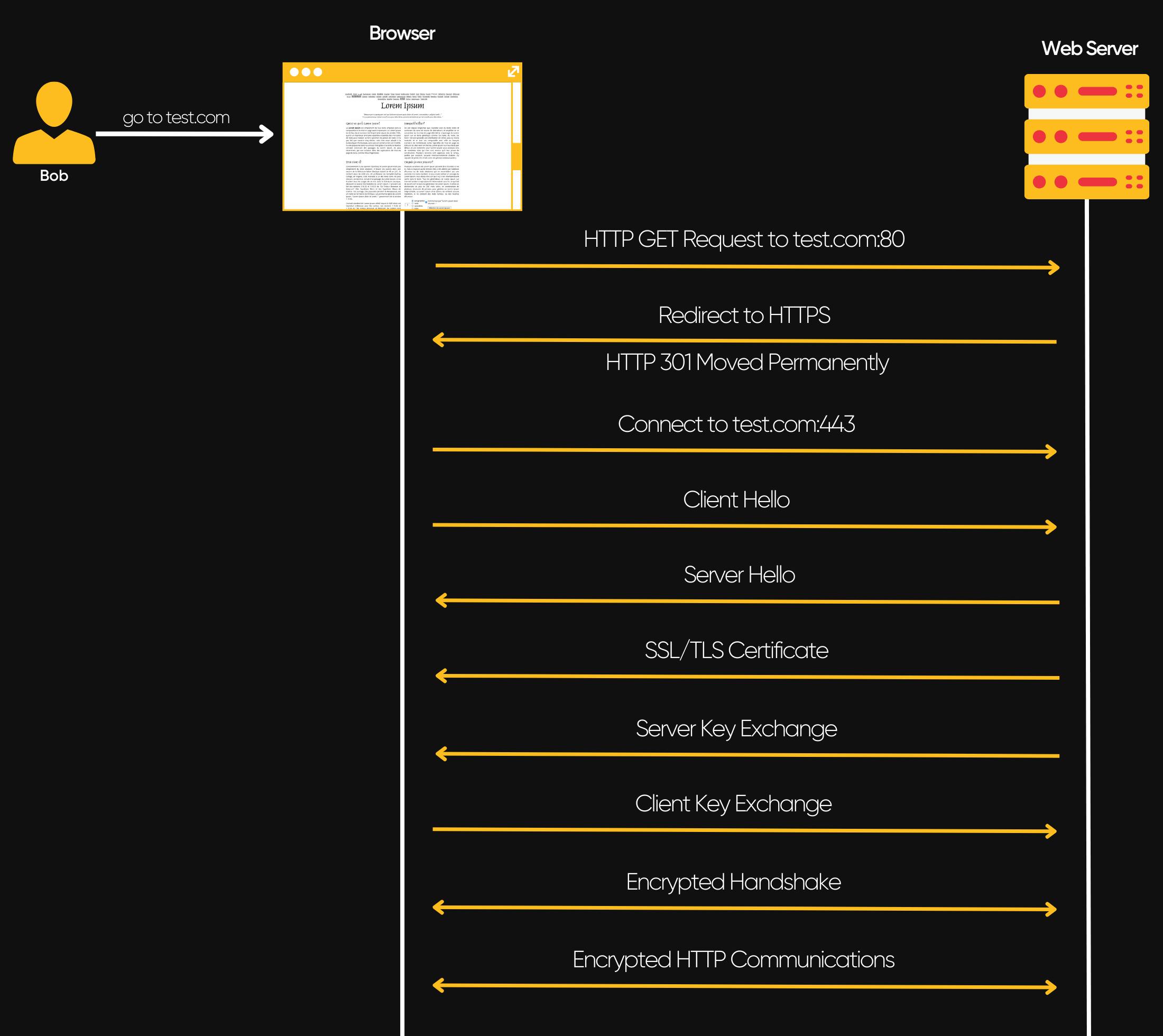
When Bob tries to visit a website that enforces the use of HTTPS using a URL starting with http://, several things happen:
The browser will attempt to resolve the domain test.com and send an HTTP request to the unencrypted port 80 of the web server.
The web server will detect the use of the HTTP protocol on port 80 and redirect the client to port 443 (HTTPS). To do this, the server will send an HTTP 301 Moved Permanently response.
Once on the HTTPS port, the client (web browser) sends a "client hello" packet that contains various information about itself, such as the encryption protocols it supports.
The server responds with a "server hello" packet that also contains various information about itself, including the encryption protocols it supports.
The server sends its digital certificate. This helps to prove to the client that it is on the correct website. The certificate contains information such as Information about the website (domain), the digital signature of the certification authority, and the server's public key.
The server then proceeds with a Secure Sockets Layer (SSL) key exchange to encrypt communications with the client.
To determine if the communications are encrypted properly, the client and server initiate a handshake.
If the encrypted handshake is successful, the client and server can communicate securely.
\Note: A bad actor can, sometimes, force the downgrade of the HTTPS connection to HTTP to make the data readable. This is known as a [downgrade attack](en.wikipedia.org/wiki/Downgrade_attack)"*
Outro
Thanks for reading, encryption is not the easiest thing to understand when we deep dive to it. However I tried to not make it too complicated.
If you want to support me you can hit the subscribe button on Instagram: h0neyp0t.sec
Don't settle for null, strive for #0...
h0neyp0t.