Table of contents
- h0neyp0t's note
- Getting Into API Security Research | Introduction & Layout
- API Security Research | Terms & Definitions
- API Security Research | What is API Security Research
- API Security Research | Why API Security Research
- API Security Research | My Experience and Background
- API Security Research | Conclusion && Summary
h0neyp0t's note
When I created my Instagram account, I didn't expect to meet so many kind and interesting people. Today, I am pleased to announce my first collaboration with a cybersecurity researcher who is driven by his passion. totally_not_a_haxxer approached me with the idea of writing an article for my blog, and I accepted without hesitation!
Getting Into API Security Research | Introduction & Layout

As the world of web and networking continues to grow, with flowing protocols, newer systems, newer mechanisms, and more, constant improvements and ways to automate those systems always become about. Well, in today’s realm, we automate the process of specific systems through Application Programming Interfaces (APIs) which are used in about every single application that you know of! Well most if not all anyway. In Today’s article, I figured I would write some basic ways and an introduction as to how and why you might want to touch API security research and why it is important! Before We Go on I would love to list some sections that we will be writing and going over to make sure you have a good idea of where you are going with this! Below are all the listed sections.
API Security Research | Terms & Definitions: A small little section that will drop all terms or the most commonly used terms within this article.
API Security Research | What is API security research: A section that talks about and explains what API security research is and gives you a bigger incite into it.
API Security Research | Why API Security Research: An explanation and single section that talks about the API security research world, why it is important, why you should get into it, a good list of examples of where APIs are used, and why and more!
API Security Research | My Experience and Background: A small section talking about my personal experience and the true fans as well as tips and tricks I learned about API security research!
API Security Research | Conclusion && Summary: A small section talking about API security research
Now without much more to say let's get into it!
Note: Before getting into this article I want you to note that this is by far the most basic article I have ever done and an introduction article that talks about the field. I need to also let you guys know that if you are even closely intermediate in this field of research, then this article may be too basic for you. I decided to take definitions and break them down to ELI5 format, something most people could understand at least to the best of my ability!
API Security Research | Terms & Definitions
Before we actually dive headfirst, I would love to get some terms down to help you understand the main points and sections in this article!
IoT: Also known as the Internet of Things pretty much defines any device with a sensor or way of communicating with the internet directly. For example, Google Chromecasts, and AppleTV are all examples of IoT devices- even cars.
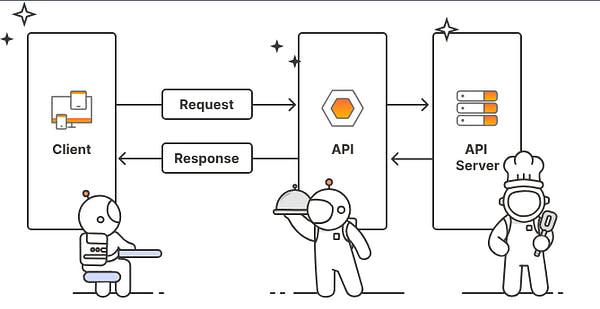
API: Application Programming Interface is exactly what the name implies, it is an interface that sits between the web server and the web application.
API Security Research | What is API Security Research
In simple terms, API security research is the research into the Application Programming Interfaces that systems and applications such as web applications use. But what about on a deeper level of things? API security research entails so many different things and in order to get into it, you need to at least understand the fundamentals of it. So this section will aim to introduce you to what API security research entails and why we use it or utilize it. So without much more to say, what exactly is an API and what does it do? Typically, the idea of an API is really a set of rules and protocols that allow different forms of applications to communicate and interact with each other! APIs are involved in everything from cars to your very small and lightweight SmartTV ( we will get into this later)! There are many different kinds of APIs that also exist depending on the context such as web APIs, operating system APIs that allow you to work with the operating systems internals, as well as software development libraries and even software that may have their own APIs that allow you to easily write plugins for it! But why does the security of APIs exist? The sole reason API security testing is its own field is because of the different types of APIs there are and the amount of implementations APIs have that are not just based in the web world! All of these need to have their own field and need to be tested accordingly. But let's focus on a specific type of API hacking and testing- The modern web. In today’s world, modern applications all use some sort of API and all have their own different chains of API’s whether or not it is for authentication or to verify and check user features on a dashboard, they just exist. In order for developers and companies to ensure the security of the APIs by ensuring that they do not overly expose information, do not break, and are not truly attackable, it's important that they can hire security researchers that know how to test them. But how can one even start? Well, in order to start in this realm, it's important to understand the basics and how these hackers may even operate, and the skills you need! Below I have made this easier to understand by chomping down some skill sets that are important followed by why!
Basic Web Recon Knowledge: This should be the most obvious, but web reconnaissance knowledge is the most important thing in API security. This is because you need to be able to understand how to explore and properly scan APIs, how to discover special services, how to properly research and assume specific information, and even how to layout a attack plan or general idea of what you are looking for. In every security field that revolves around defending and even attacking systems, recon is a part of it. Not only does recon provide you with the proper information to get down with your attack but it can also give you a good idea of what to target first so you are not all over the place and give you an even better idea of how everything works. During this process especially in API hacking, it is important that you get a base knowledge of using tools such as Burp Suite, Postman, and other tools that may be used to explore APIs or other web-related services. These tools also help with automating the discovery process or detailed process where API hacking really comes to be a pain sometimes! But do not get discouraged! It's super fun!
Basic Understanding Of Web Security: Of course, APIs have their own vulnerabilities such as BOLA, BFLA, BUA, and other various vulnerabilities. So, in order to fully understand how one might go about exploiting vulnerabilities, it is important that you have a basic understanding of web security and general vulnerabilities such as XSS, SQLI, SSTI, CSRF, and other concepts and vulnerabilities. I typically suggest that you get started with OWASP’s top 10 list as it's a good starter path.
Basic Understanding Of Web: A basic understanding of the web goes an extremely long way. This is because when exploring API you may need to use specific tools and developer utilities that all interact with the web and also understand how to use consoles and other utilities to get more information on the API you are trying to explore.
Basic Understanding Of How To Exploit Security Weaknesses: As mentioned above, understanding how exploitation works such as the process and the direct development of them is something that you should have locked down. It's a super handy skill and while some API vulnerabilities are just easy to bypass without an exploit and simply just entering a character or finding a specific path; then being able to work around it all is going to be super helpful!
There is also a menu of other descriptions of API hacking and what API security is, but let's sum up with this. Hacking can mean different things to different people and the term “ security research “ is all dependent on what you want to do and also what field you are into. In general, the term does stay the same but can be used in different contexts. Now let's move onto a much more different section, let's talk about why.
API Security Research | Why API Security Research
Strap your seatbelts on, this might be quite the ride O_O! The world of API security is growing larger and larger every single time we blink or maybe even breathe! But why is it growing so rapidly? Why is it such a big deal and why is it the hotter deal? Well, this is simply due to a matter of growing technologies in the automotive world! As more and more devices especially IoT devices become web-based and extend their functionality past the barriers of hardware and basic communication, the web becomes a massive part of this. This also means that APIs are going to become more and more common. Let me get this directly straight before we dive into this section more, I will be using IoT devices as a prime example of API but I have listed some other examples of where APIs also exist.
Web Applications: Web applications use APIs all the time to do thousands of different things, especially if they are hosting their own frameworks or tools that can be integrated into other applications.
Automobiles: This is a part of IoT but automobiles are absolutely saturated with systems that utilize APIs such as radio systems, management systems, environmental control systems, and more! These APIs can help cars easily interface with the information from the outside and the inside of the vehicle- to put it lightly.
Social Media: While also counted as a web application ( in most cases ), social media applications widely have adopted APIs because of how lightweight and extremely fast, and portable they can be.
These are just some basic systems. So here is the deal with IoT to put it lightly, almost everything in our everyday life can be IoT. Take the following list of devices as a primary example of what IoT devices consist of.
Smartphones, Smartwatches, Smart TVs, Smart Thermostats, Smart Home Security Cameras, Smart Door Locks, Smart Lighting Systems, Smart Speakers, Smart Refrigerators, Smart Washing Machines, Smart Air Conditioners, Fitness Trackers, Smart Smoke Detectors, Smart Doorbells, Smart Pet Feeders, Smart Irrigation Systems, Smart Home Hubs, Smart Garage Door Openers, Smart Water Leak Detectors, Smart Power Outlets, Smart Vacuum Cleaners, Smart Garden Sensors, Smart Baby Monitors, Smart Coffee Makers, Smart Mirrors, Smart Air Purifiers, Smart Kitchen Scales, Smart Planters, Smart Sleep Trackers, Smart Lockers.
These are just some very basic counts of devices but are a good example. Now why are we talking about IoT when we need to be focusing on API security? As mentioned before, all forms of devices, or most anyway will require or use some sort of API especially if they are considered “smart” devices such as the smart TV’s you buy from Google, Apple, Roku, and other various brands. This is because they need a super fast, robust, and lightweight way of working with the outside world and even working with other devices! For example, say the AppleTV needs to ensure other devices have the specified information about the TV itself to create proper sessions. The AppleTV may host a web server on itself that is filled with APIs dedicated to pulling information which acts as a chain of APIs tied to one primary API that other devices would make requests to after broadcasting itself on the network using protocols such as SSDP. Because the world of IoT at least in today’s society uses so much and has so much functionality to it, we need to make sure that information about those services, protocols, devices, and functions are all extremely easy to access over a network and API’s are just the way to go for that. Let's go ahead and take it another example. Say you have a google chromecast device that needs access to real-time data on Google’s servers such as the current weather based on the current geolocation of the device. The device would make remote requests to Google’s servers with specific authentication settings to fetch the data from their own internal APIs that store data of a region such as the weather based on the given location and may allow devices to retrieve information from that API. That is a short but small example as to why IoT devices require APIs ! But- wait…we may have gone far from the point, why should YOU work with API security? The point when talking about IoT security was to show you and get you to understand the mass amount of systems and devices that utilize APIs and why they need to. because of this with a mix of not enough knowledge in API hacking and it just recently becoming popular- there are still devices, literally millions, and the same with web applications that have probably the simplest vulnerabilities out there because their API was miss-configuration properly. For example, take the story of David Colombo who at 17 was able to hack a Tesla simply just because of a simple API misconfiguration in the vehicle.
These are just some good examples of where API hacking may actually become handy. Not only are they used in nearly every system to date but they are also extremely weak right now due to horrible implementations and how rushed APIs are in today’s world! So, maybe it is something you should take up!
API Security Research | My Experience and Background
So, I have a separate article for this and have had and made even talked about literally research papers worth of work for this but I figured why not make it a little bit more unique. So, the first time I got into IoT security research was when I was browsing on GitHub trying to find projects I can remake that were in another programming language than the one I was going to rebuild it in. For context, back when I started programming and when I was learning languages like Ruby and Perl even something as much as C++, I would start learning the language by being able to recreate smaller or even medium-sized tools that were security-related I found on GitHub. This is because it trained my ability to work with the language I was trying to master and gave me a much more unique experience! To this day I actually teach people how to port code because it is quite important and a great way to practice. Anyway, besides the point, I came across this framework that would shut off a Samsung CMS TV simply by making an empty HTTP post request to one of the endpoints on the device. Now, I did not have any other proof it worked other than assuming it did based on the source code, so I did a little bit more research. After digging for what could have been over 8 hours, I could not find any exploit or vulnerability that this was — so in my mind I labeled the code as broken and that it was just a weird “attention grab” for people and just moved on. When I was about to shut my PC off for the night I figured I would just give it one more page, one more search, and one more scrape. When I did, I came across something that actually blew my mind and it was not exactly for that device but something different. It was a post that read the following brick
So I’m working the other day, and my wife asks me why the TV is on. I don’t know. I didn’t turn it on. But it’s near my desk, and I know nobody else turned it on, either. I had been running Nmap
on my local network to test something out, though. You may have heard that you want to be careful using Nmap against printers because some of them will studiously print out the packets they receive and you may not want to use up all that paper. Was my Apple TV doing something like that?
Turns out it was. Join me for a little investigation-as-excuse-for-practicing-tools. I find chasing my own questions teaches me more about how things work than reading a book or in some other way chasing other people’s questions.
If you have an AppleTV, do this: Find out its IP address (Settings > General > About > IP Address. Mine was at 192.168.10.110. While you’re here, see if you have model A1625, running tvOS 9.2.2, as I do — maybe it matters?), then shut it off. Then, using a computer on the same network, run an Nmap version scan.
This post was the one thing that forced me to instantly start getting into IoT security. I then spent the rest of the night reading more into occurrences that had happened over the night and just could not stop! The next morning I was like 10 different articles and blogs deep ( all of which were much older research papers) and I could not stop reading all of this cool information about it. Eventually, I started to learn how IoT hacking can work and how someone could get into it. For someone like me at the time, there is not so much in that realm of things and not that much education for beginners. So, I eventually forgot about it and said to myself “I will come back later”. So, fast forward roughly a few months and I start working on a very outdated framework of mine and figured I should first start working on remaking one of the most important modules in that script- data sniffing. For context, this framework for me personally got over popular and I felt that what I gave people was just wrong and was way too buggy for people to even bother downloading. So, I said, yk what? I am going to give it one last shot and see if I can make something better. Well, this road quickly got turned around. The module I was working on this module allowed people to sniff data such as passwords, images, files, and so on from the network. Since I could not find specific packet captures and at the time was too paranoid to even bother opening or downloading them, I set up my own servers and unique systems that could all be easy to sniff data from.
<Direct Snippet From Caster — SkyLine’s Proof>
I opened up Wireshark and listened for packets from a specific host ( my PC ) and then set some filters on it. After that, I also had a test run of a second module known as the HTTPSniper which would “snipe” or “scope” out HTTP requests within networks. The program had to spit out this massive URL that came from a RokuTV that I had in my room, and it was a singular URL that just did nothing ( from my point of view ). After inspecting the URL a bit more, I figured out that the endpoint was part of a system setup that was setting up specific networks.
This led me down quite the road path. During this discovery, my idea and what I could do with IoT truly kicked back up again. I went from Roku to finding an interest in any smart TV or smart device I had myself. For more on that story directly and all of its details I will go ahead and link that article here. But, in the end, the security research had lead me down quite a deep path and even led me so far that I had to organize 300 pages worth of research! This is where it all got real, but as I mentioned, the article on caster fills out the details more. Today, I am more focused on talking about where it led me. In this field and especially in today’s world with all the energy I also have, I go for anything in this field. If it is IoT security, Automotive security, or something as much as solidity smart contract auditing- I go for it and I never stop. This story lead me into the world of realizing that there is so much out there to explore and actually most of the cool things to research or look into are going to be IoT devices, not to mention; it is kind of cheap in some shape or form. However, here is what IoT security made me realize. It made me directly understand that there are a ton of skill sets out there, but with the way the world is going- there are some important ones that top the list; for that, the 5 are listed below.
Reverse Engineering: You may be confused by this, but reverse engineering? Really? Yeah, and no not traditional reverse engineering, not just protocol reverse engineering, not just firmware reversing — but all of it. Yes, all of it. When it comes down to the specifics of IoT you will realize that reverse engineering will help you a ton for various purposes. The first one is understanding how to reverse engineer and work with different proprietary protocols and systems. During my AppleTV security research, I had to attempt to reverse engineer multiple systems and one of those included the AirPlay protocol and get a deeper understanding of how it works and write my own documentation which turned out to only be 50 pages of slowly progressing research but that is a good example. The reason I had to do this was that I needed to understand how the service and the protocol worked together, what they did internally, and the data it could hold in case I needed to make my own program to work with it which in the end even included downloading SDK’s by Apple and being able to work with them. The second part of reverse engineering came down to understanding how proprietary services and systems worked. While I did not fully understand everything I was doing, I needed some decent knowledge of how to dissect applications and how to really chomp down all of what was happening.
API Security / Web Security: API and web security are huge ones. I have noticed this in about every field I have ever studied and as much as I hate to admit it — the web is everything and will be the future. The web is about in everything we do, hell, even your silver 2000 Mazda Miata has the web in it. Why is this? Specifically, when it comes to IoT which includes practically and nearly every device we work with today, they need a special system to communicate with them, something that is fast, something that does not need to maintain state (RESTful) and something that is easy to work with, chain together, operate, manage and well something that is also quite reliable. Because of the increasing need for this type of system, APIs are the one thing to be slapped onto a chain and immediately passed down. So understanding how APIs work, and understanding common flaws and vulnerabilities with them is extremely important. That along with general web security is extremely important because you need to understand how to look for services, how to research specific services, how to send requests to services such as RTSP services, and also understand how to exploit common web vulnerabilities such as XSS, NoSQLI/SQLI, and also vulnerabilities such as XXE. All of these are quite crucial to learn because of how insanely dependent IoT devices such as Google Cast, Nest or even Amazon IoT devices are on the web and APIs — but again, those are not the only ones that depend on the web.
Protocol Analysis: Protocol analysis I have already talked about. But when you get deeper into IoT you will understand that properly working with proprietary or even custom implementations of protocols is quite important if you want to hit more network hacking side of things than you do the hardware/firmware side of things. This includes understanding how to analyze protocols, understanding how layers work in protocols, and being able to spot configuration issues within those protocols which can boost your security research quite ALOT!
File Forensics: File forensics is one you are going to be confused about, but I will say this; you do not need to master that skill but it is important. File forensics is the skill of analyzing specific files, recognizing specific magic bytes and codes, understanding how files work, how to create them, and how different files may work. A lot of times, companies like Apple, Amazon, and Google create IoT devices that all rely on their own custom format and even APIs. You might be wondering why you would even need this if you are not going to always be going so deep to gain access to the system like that- but damn cowboy chill! I have not gotten there yet, give my turtle speed a second hahaha. When working with specific services such as and in AppleTV’s case AirPlay, you will notice that some responses will not be web pages, instead, they will be files that vary in all shapes and forms. In the one case I was working with AirPlay I had to figure out how to parse and build my own program and library to marshal binary properly list (BPLIST) files because those were the ones that were downloaded from the server. Without a common understanding of everyday tools such as the ones used to extract, cut and verify files, I may not have actually been able to properly work with that file format and not to mention the many other ones that were nowhere to be found that came from other services on other devices such as third party home security cameras! So it is quite important to understand how to use specific tools to analyze files and other forms and types that are hidden out there hahaha!
Programmatic Knowledge & Logical Comprehension: This one is a huge one for me but I think anyone in tech especially security should learn how programs work, how services may work, and how general systems may work. If you are not new here, you may have seen me post many times about concept logic, concept understanding, logical processing, and more. I have not however even done an article explaining why this is important. So, let me do that. Within the world of programs and security comes a world of black-boxed scenarios and trashy documentation. Because of this, breaking systems and trying to find complex vulnerabilities is extremely hard and just not worth it to some people because they lack the logical understanding of how specific programs work. For example, anyone can build a simple login application and they all work differently, but the concept will stay the same and the implementation will differ. Having a conceptual understanding of how the concept works and how the general idea of the application works will not only make your process of understanding much faster but also help you understand what you need to look for and why.
Overall, when working with IoT security and especially digging myself as advanced as possible when working with specific devices I was able to fully understand and take advantage of my environments to learn more! I even have a slight tip for you that may help you get into it more. When I started security research and even programming with no experience, I found that throwing myself at the most complex machines or even intermediate machines I have never been able to hack before was the best- this is because someone like me could come about and write a bunch, develop all of these systems, however — they may be different, they may not know HOW to do something but they may know WHAT something is. I found that again after throwing myself at those boxes that the experience is worth more than 1,000 quizzes. Learning about fields is a great starter, but you will never get anything more valuable in these fields than throwing yourself into even real-world situations such as this IoT security research I talked about. Now that we have that out of the way, let's end this article properly.
API Security Research | Conclusion && Summary
Okay, so let me clear something up. You may be asking “The article was about API security research, not IoT?” –You are correct on that, towards the end I went DEEP into IoT hacking and security, but for a good reason. You will find that most devices today are considered IoT and all of those devices may also be using an API, similar to how 90% of web applications today ( that is invalid and not the full direct nor is it the most scientifically backed percentage so do not take it seriously ) use and run on API’s. This is because APIs are quite essential to how computers can work with data! With this, it is important that it not only tells you about API security research but also gives you a reason to look into it, and I personally always felt that the most fun was in researching IoT devices due to the number of third-party systems and APIs they use! But, anyway, concluding this article: The world of APIs is quite massive even if it is small — it is according to some people “still new” which is not fully wrong, yet there is so much to explore and so much cool systems and training labs where they spend their time working on understanding and researching into API’s.

Ending Note — Extra’s, Resources, Support, Thanks
Typically I never do like promoting stuff but I figured it was worth a shot. This section will provide you with basic information about me, some socials you can follow me on, how you can support me, and some resources that were used to build this article/module. Apparently, my articles are so long people are calling them “modules” so I will go with that for now hahaha! Below are some bullet points that showcase extra sections.
Ending Note | About Me → This section will talk obviously about me, who I am, why I am doing this, current projects, etc.
Ending Note | Thank You → A section thanking you for reading this article and explaining why I value community.
Ending Note | Ways To Support → A section talking about ways you can support me with currency!
Ending Note | Where To Find Me → A section that talks about where you can find me and how you can follow me.
Ending Note | Resources To Advance Your Knowledge → A section that explains some basic resources used to help you.
Below, sections are listed and talked into!
Ending Note | About Me
Hello there nerd! My name is Ryan and I am commonly known as Totally_Not_A_Haxxer! I am a 16-year-old security researcher and developer with quite the experience primarily in development (50+ languages including working on my own) and take a huge interest in automotive security! I write the articles I write especially in length as well as books because I believe that knowledge is for everyone and should not really be charged so much. For example, I saw someone write a Golang tutorial that was like 10 hours of content and charged over 1K for it- I thought it was a complete waste of time so I started my blog page to not only do what they were doing but do it better and for free! I also have multiple projects going on around education such as $1 Courses which are courses on various topics in tech or even general that get sold off for a single buck! That is a small about me, you can find more which we will get into in quite a second hahaha!
Ending Note | Thank You
I want to also thank you for reading the article and coming this far, I know these articles are extremely large and take a ton of time but I hope they were worth it. I do try my best to actually go and put the time and effort into the articles by ensuring that I can actually help educate people and go deep into the topics I talk about for free! So, if you have made it this far, I appreciate giving the effort back as far as reading the article and hoped it helped :D!
Ending Note | Ways To Support (Financially)
Currently, I am not in the best of situations with money and I do not have the proper funding to afford good equipment for security research even something as much as a laptop where I could do remote work. That being said, I have always been used to saying “I do what I do with passion, and I will stop at nothing to do so”. Even though I do not have direct resources, I always do try my best to deal with what I have and do what I want to do with said resources I do have. With this, I ask that if you can bother to donate or do have the extra to spare, this will make my development, skill, and more go much MUCH faster and also make me much more motivated to continue doing what I am doing! Below I have listed my cashapp and Venmo as well as crypto wallets!
-
BitCoin Address: bc1q45ctj3cwl8zr2qdw4xceukr58cdnayxuutymt8
Ethereum Address: 0x466BA936E2bdbEab74c8cd048CC43279fE712E54
USDC Address: 0x466BA936E2bdbEab74c8cd048CC43279fE712E54
Tether Address: 0x466BA936E2bdbEab74c8cd048CC43279fE712E54
XRP Address: r4s8FeyYCBHJQGJRGuDuPeM2YLMwRCZP4R
Ending Note | Where To Find Me
This sounds weird to say, but you can find me in a few places; social media is one of them. Below I have listed some links of where to find me but I will say this. Often in discord servers, communities, and even other platforms: some people always ask me for links and I can get tired of constantly pasting social media links on days when I have a bunch of stuff to do and given social media is not on my phone ( at this time, working on a study/ghost month ). SOOOO, that being said, Google is a good place to go literally search “Totally_Not_A_Haxxer” and some of my socials should pop up + look at it this way, you get more OSINT experience.
Since this article was on API hacking, I would like to give you a good idea of some general resources and where to start with it! You might see some familiar or well-talked-about resources on this list.
Sorry to say but there were not much other lists I could find, I had a few more but they were seriously not good choices and I do not think would be worth it to link!